Someone just learned the most expensive lesson in crypto history. A single copy-paste error cost them $50 million.
This wasn’t a hack in the traditional sense. The blockchain worked exactly as designed. But the attacker exploited something far more vulnerable than code: human behavior.
The $50 Test That Triggered Disaster
The trader did everything right at first. Before moving millions, they sent a $50 test transaction to verify the destination address.
Standard practice. Smart precaution. Fatal mistake.
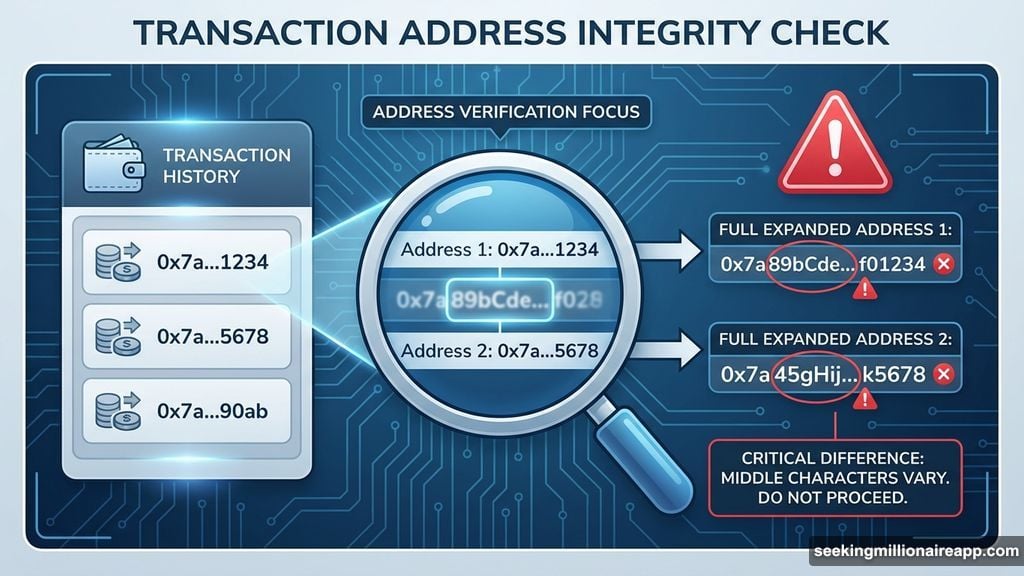
That tiny test transfer alerted an automated attack script. Within seconds, the attacker generated a fake wallet address designed to look nearly identical to the real one. The first and last characters matched perfectly. Only the middle section differed.
Then the attacker sent a negligible amount of crypto from that spoofed address to the victim’s wallet. This placed the fraudulent address directly into the trader’s recent transaction history.
Where Visual Shortcuts Become Deadly
Most wallet interfaces display abbreviated addresses to save screen space. You see the first few characters, then “…”, then the last few characters.
Makes sense for usability. Creates perfect conditions for fraud.
The victim glanced at their transaction history. Saw an address that started and ended correctly. Copied it without checking the full string.
So instead of sending 49,999,950 USDT to their secure wallet, they sent it straight to the attacker. The transfer completed in seconds. No blockchain could reverse it.
Attacker Covers Tracks Fast
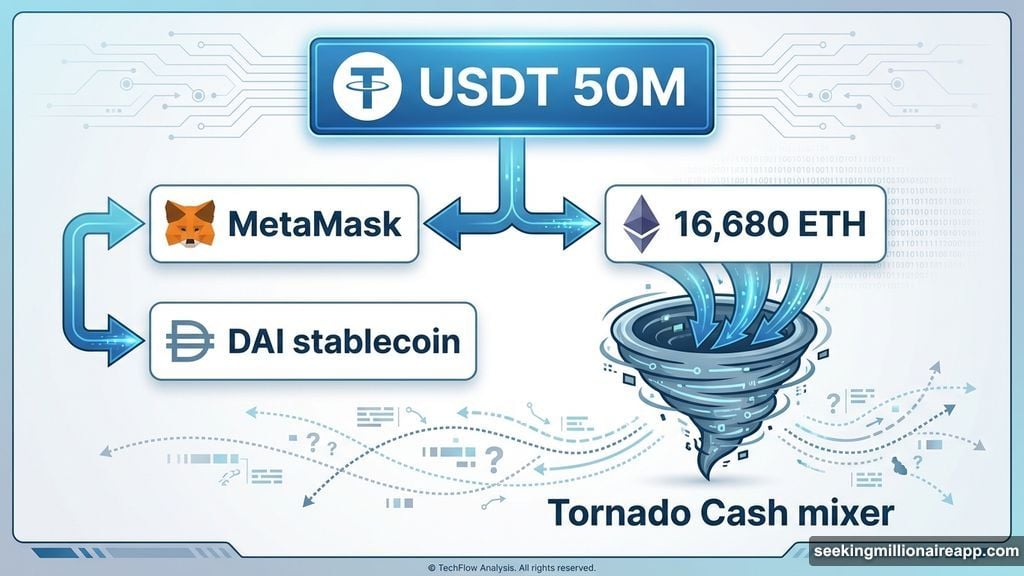
The criminal knew they had minutes before anyone could freeze the assets. USDT’s issuer can blacklist stolen tokens.
First move: swap all USDT for DAI stablecoin using MetaMask. DAI can’t be frozen by a central authority.
Second move: convert DAI into roughly 16,680 ETH. Ethereum offers better mixing options.
Third move: dump everything into Tornado Cash. The decentralized mixer severs the visible link between sending and receiving addresses. Law enforcement hates it. Privacy advocates defend it. Attackers love it.
The Desperate Bounty Offer
The victim sent an on-chain message offering $1 million to get back 98% of the stolen funds. That’s a white-hat bounty, typically used when hackers find vulnerabilities and return funds for a reward.
But this message came with threats. The victim claimed they’d already filed criminal charges and gathered “substantial intelligence” about the attacker’s identity.
“You have 48 hours to comply,” the message warned. “Otherwise, we pursue relentless legal action through international law enforcement.”
Empty threat or genuine leverage? Hard to say. Tornado Cash makes tracking nearly impossible. So the $1 million offer might be the victim’s only real option.
Why Address Poisoning Keeps Working
This attack method isn’t new. Security researchers have warned about address poisoning for years. Yet it keeps claiming victims.
The problem isn’t blockchain security. The technology works perfectly. The weakness lies in wallet interface design and human psychology.
Wallet apps abbreviate addresses for clean visuals. Users rely on pattern recognition instead of full verification. Attackers exploit that gap with surgical precision.
Plus, the attack automates instantly. The moment someone sends a test transaction, scripts can generate spoofed addresses and contaminate transaction history within seconds.
Three Defense Layers That Actually Work
Want to avoid becoming the next $50 million cautionary tale? Stop relying on visual shortcuts.
First, verify the complete address character by character. Yes, it’s tedious. Yes, wallet addresses contain 40+ random characters. But losing millions is more tedious.
Second, use address whitelisting features. Many wallets let you save trusted addresses. Send only to pre-approved destinations. This eliminates the risk of copying contaminated addresses from transaction history.
Third, never copy addresses from transaction history. Treat that list as potentially poisoned. Always copy addresses from the original source where you first saved them.
Some wallets now offer enhanced verification tools. Checksums, QR codes, and ENS names provide additional safety layers. Use every available protection.
The Real Cost of Convenience
Wallet developers face a brutal trade-off. Make interfaces too complex and users make mistakes. Make them too simple and attackers exploit shortcuts.
Current designs prioritize visual cleanliness over security. Abbreviated addresses look professional. They’re also deadly.
But fixing this requires rethinking wallet UX from scratch. Full address displays clutter screens. Character-by-character verification frustrates users. Better verification tools add friction to every transaction.
So wallet teams keep shipping products optimized for convenience. Users keep falling for address poisoning attacks. The cycle continues.
Why Crypto’s Permanence Cuts Both Ways
Blockchain’s core feature is also its biggest liability. Transactions can’t be reversed. No customer service department can help. No chargeback option exists.
Traditional banking has fraud protection because transactions can be unwound. Someone steals your credit card? The bank reverses the charges.
Crypto eliminates that safety net by design. Immutability prevents censorship and creates trustless systems. But it also means one mistake costs everything.
For traders moving millions, that permanence demands paranoid attention to detail. Yet human nature resists that level of constant vigilance.
The Lesson Nobody Wants to Learn
This attack succeeded because the victim got comfortable. They’d probably sent thousands of transactions using the same shortcut method.
Test transfer, copy from history, send main amount. Quick and efficient. Worked perfectly every time.
Until it didn’t.
That’s exactly how address poisoning claims victims. The attack targets experienced users who’ve developed convenient habits. Newcomers who laboriously verify every character are often safer.
So the real vulnerability isn’t technical knowledge. It’s the false confidence that comes from repeated success.
Check every address. Every time. No exceptions. Your first shortcut might cost $50 million.
