A crypto investor just lost $12.4 million in Ethereum. The attacker spent two months planning the theft.
This wasn’t a quick hack. The scammer patiently monitored the victim’s wallet activity for over 60 days. Then they struck with a sophisticated “address poisoning” attack that exploited how humans verify wallet addresses.
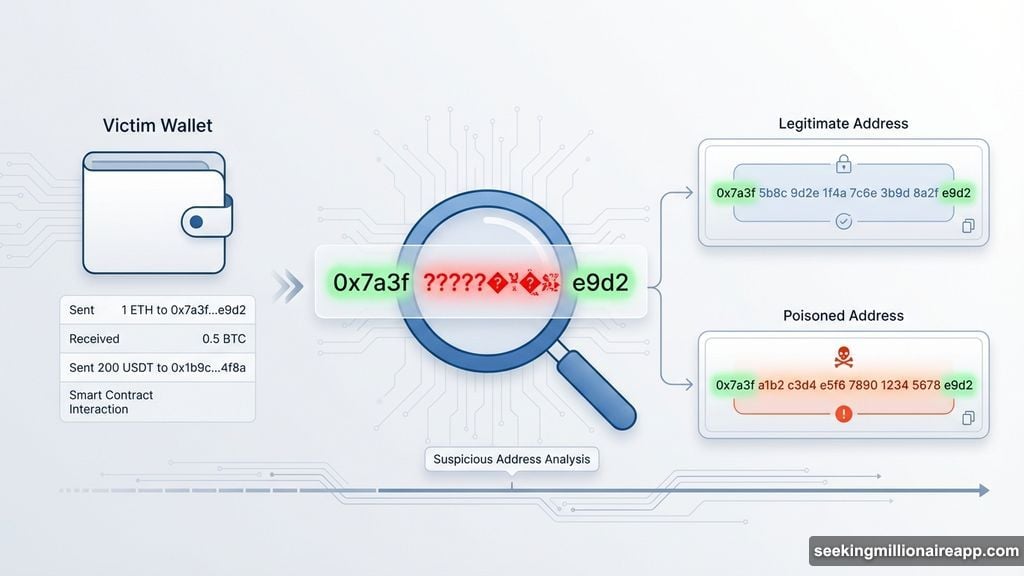
The victim copied what looked like the right address from their transaction history. But it was a fake planted by the attacker. The funds vanished into a fraudulent wallet designed to look nearly identical to the legitimate one.
How the Two-Month Setup Worked
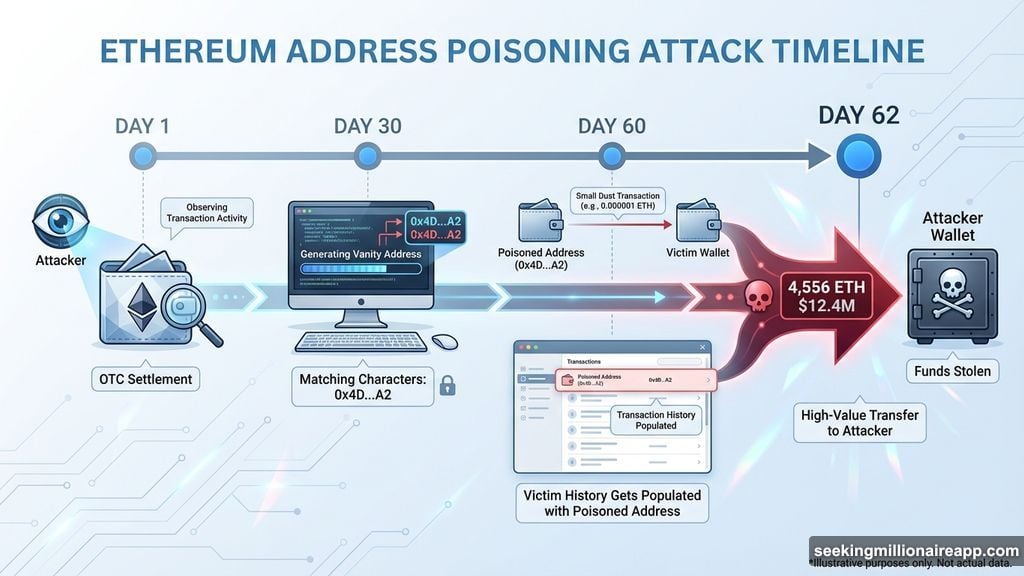
The attacker didn’t rush this operation. They observed the victim’s on-chain behavior carefully.
First, they identified a specific deposit address the victim used for OTC settlements. This address received large transactions regularly. So the attacker knew it would be copied again eventually.
Next came the preparation phase. The hacker used vanity address generation software to create a look-alike wallet. This fraudulent address matched the legitimate one’s first and last characters exactly. The middle section differed, but most people never check those characters.
Then the attacker “dusted” the victim’s wallet. They sent a tiny transaction from the poisoned address. This populated the victim’s recent activity log with the fake address.
The dust transaction happened 32 hours before the theft. That timing proved crucial. The fraudulent address sat at the top of the transaction history when the victim needed to move funds.
The $12.4 Million Mistake
When the victim prepared to send 4,556 Ethereum, they followed standard practice. They checked their recent transactions to find the OTC deposit address.
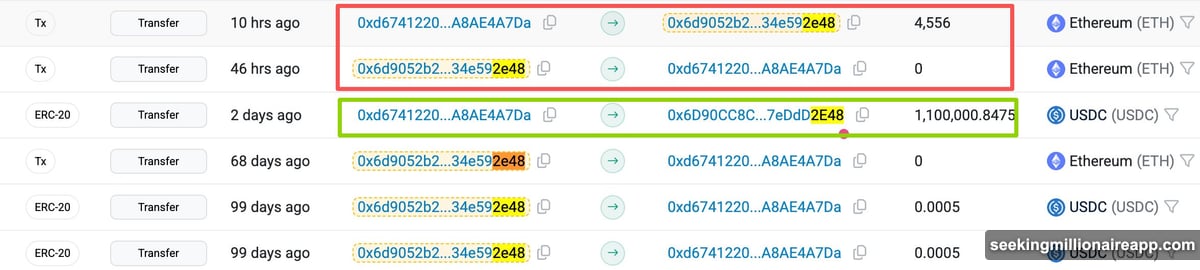
The poisoned address appeared legitimate at first glance. The starting characters matched perfectly. The ending characters looked identical too. So the victim copied it without verifying the middle section.
The funds transferred immediately. But they went to the attacker’s wallet instead of the intended destination. By the time the victim realized the error, the Ethereum had already moved.
Blockchain analyst Specter tracked the entire sequence on-chain. The attack showed clear premeditation and patience. The attacker invested months of monitoring for one massive payday.
Why Address Poisoning Attacks Are Spreading
This marks the second eight-figure theft via address poisoning in recent weeks. Last month, another trader lost approximately $50 million using the same method.
The attacks exploit how wallet interfaces display addresses. Most wallets truncate long hexadecimal strings to save screen space. Users see only the first few and last few characters.
That design choice creates vulnerability. The critical middle section where addresses differ gets hidden. So victims comparing addresses see only the matching beginning and end.
Moreover, users rely heavily on transaction history for repeat payments. That habit makes address poisoning especially effective. The attacker plants a fake address in recent activity, knowing victims will copy from that list.
Scam Sniffer reports these attacks are proliferating because the technique works consistently. Security watchers say the success rate remains high even against experienced crypto investors.
The Institutional Investor Question
This breach raises concerns about verification protocols. The victim moved $12.4 million in a single transaction.
Institutional investors typically employ strict security measures. They use whitelisted addresses and test transactions before moving large amounts. Yet this victim apparently skipped those precautions.
That suggests either retail-level security practices or a catastrophic verification failure. Either scenario points to serious gaps in standard operating procedures.
Professional traders often face pressure to move funds quickly during market opportunities. But speed can’t justify bypassing basic verification steps. Not when millions are at stake.
The incident demonstrates that wallet balance alone doesn’t indicate security sophistication. Even holders with eight-figure portfolios can make elementary mistakes.
Three Critical Prevention Steps
Security experts say address poisoning attacks are entirely preventable. The key is breaking reliance on transaction history.
First, use verified address books exclusively. Hard-code legitimate addresses into your wallet software. Never copy addresses from transaction history or recent activity logs.
Second, verify every character before sending. Don’t just check the first and last few digits. Compare the entire address character by character. Yes, it’s tedious. But $12 million losses are more tedious.
Third, always send test transactions first. Move a small amount to verify the address works correctly. Wait for confirmation. Then send the larger sum. This two-step process costs minimal fees but prevents catastrophic errors.
Scam Sniffer urges investors to abandon convenience features that prioritize speed over security. The “recently used” address list creates more risk than it saves time.
The Vanity Address Problem
Address poisoning works because generating look-alike addresses is relatively easy. Vanity address software can create millions of addresses per second.
Attackers don’t need to match entire addresses. They just need to match enough characters that truncated displays look identical. With modern computing power, that takes minutes or hours, not days.
The Ethereum address space is enormous. But birthday paradox mathematics make collisions more likely than intuition suggests. Matching the first six and last six characters is computationally trivial.
That means every Ethereum user is potentially vulnerable. The only defense is rigorous verification practices. Interface improvements might help eventually. But they won’t eliminate the fundamental risk.
What This Means Going Forward
Address poisoning represents a new class of social engineering attack. It exploits human psychology rather than software vulnerabilities.
The attacker didn’t break any encryption. They didn’t exploit smart contract bugs. They simply understood how people verify addresses and created a trap that looked legitimate.
That makes these attacks particularly dangerous. Traditional security measures like hardware wallets and multi-signature schemes don’t help. The victim voluntarily sent funds to the wrong address.
Expect more incidents as attackers refine these techniques. The two-month observation period shows sophisticated threat actors are investing significant time into individual targets.
Your transaction history is now a liability, not a convenience feature. Treat it as compromised by default. Verify everything independently regardless of how familiar an address looks.
The crypto space moves fast. But security protocols can’t afford to prioritize speed over accuracy. Not anymore.
