The crypto industry just survived one of its worst months on record. January 2026 saw roughly $400 million vanish into thin air through exploits, hacks, and scams.
But here’s the brutal part. A single phishing attack accounted for over 70% of those losses. One person lost $284 million because they trusted the wrong customer support message.
That’s not a protocol vulnerability. That’s human error weaponized at scale.
One Victim Lost $284 Million to Fake Support
Blockchain security firm CertiK tracked 40 separate incidents throughout January. Together, they drained approximately $370 million from the crypto ecosystem. Add in a late-month $30 million breach of Solana-based Step Finance, and the total climbs past $400 million.
However, one attack dwarfs everything else combined.
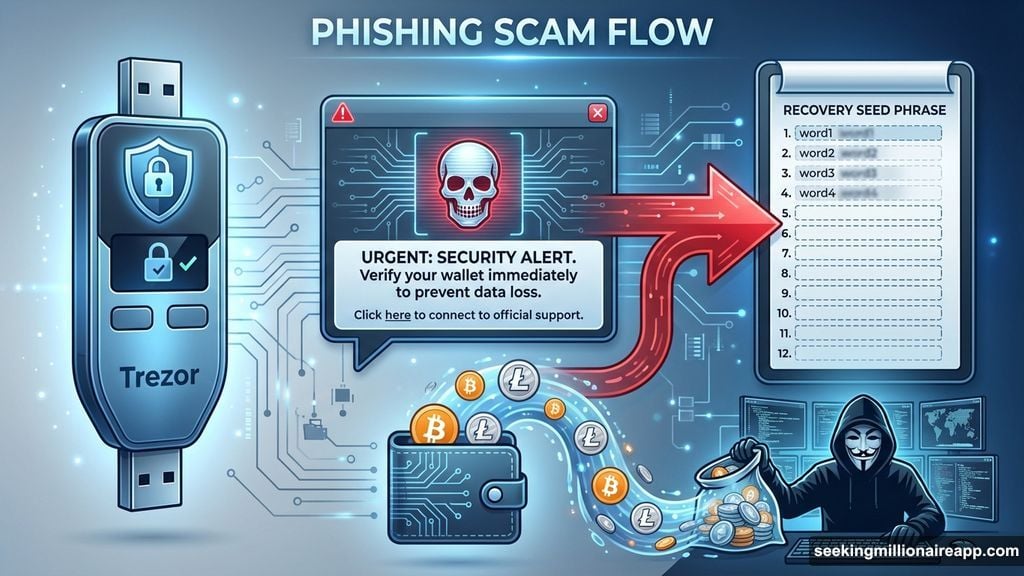
On January 16, a single investor lost $284 million after falling for a sophisticated phishing scam. The attacker impersonated Trezor customer support and manipulated the victim into revealing their hardware wallet’s recovery seed phrase.
Once they had that information, the theft took minutes. The hacker immediately drained 1,459 Bitcoin and 2.05 million Litecoin from the compromised wallet.
Think about that for a second. Hardware wallets represent the gold standard of crypto security. They’re designed specifically to protect against remote attacks. But none of that matters when someone voluntarily hands over their recovery phrase.
Plus, the attacker didn’t just disappear with the funds. They immediately converted the stolen crypto into Monero, a privacy-focused token that obscures transaction history. That mass conversion triggered a temporary rally in Monero’s price, highlighting how illicit activity can still drive market movements.
For regulators trying to track stolen funds, Monero represents a dead end. Once assets convert to privacy coins, the trail goes cold.
Smart Contract Vulnerabilities Still Drain Millions
Beyond phishing attacks, protocol-level vulnerabilities continue to bleed the industry dry.
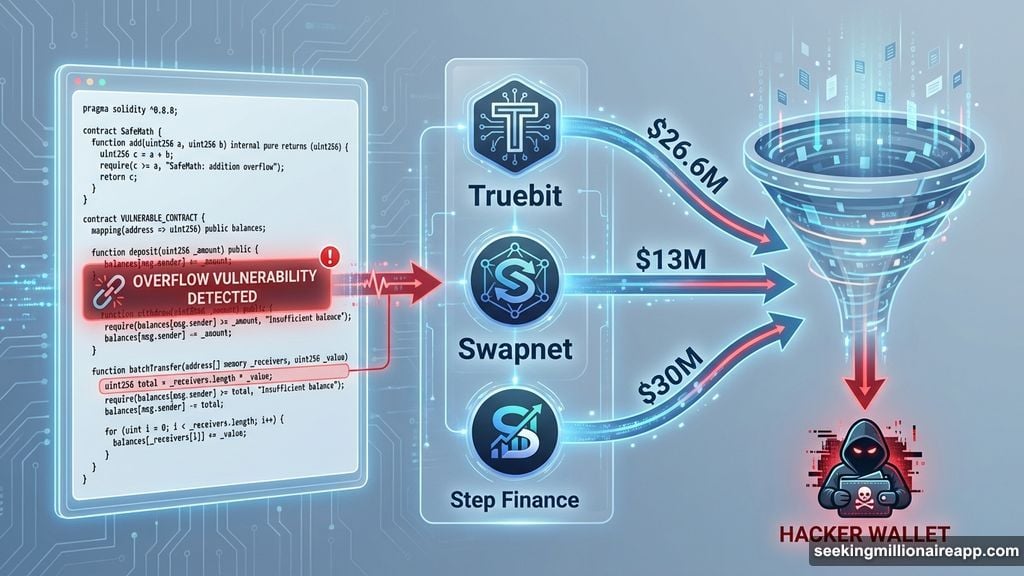
Truebit suffered the month’s largest smart contract breach. An overflow vulnerability in their code allowed attackers to drain $26.6 million. That’s not social engineering or user error. That’s a fundamental flaw in the protocol’s architecture.
Other notable victims included Swapnet, which lost $13 million to a similar exploit. DeFi protocols Saga and Makina Finance lost $6.2 million and $4.2 million, respectively.
Then there’s Step Finance, which saw hackers drain 261,854 SOL from several treasury and fee wallets on January 31. The team called it a “sophisticated attack” using a “well-known attack vector” during Asia-Pacific business hours.
That phrasing matters. Calling something a “well-known attack vector” means the vulnerability wasn’t novel or particularly creative. The attackers simply exploited a security gap that the industry already knows about but hasn’t fully addressed.
That’s arguably worse than discovering a new vulnerability. It means platforms continue to launch with preventable security flaws baked into their architecture.
Private Key Compromises Remain the Biggest Risk
January’s losses reveal an uncomfortable truth about crypto security. The most devastating attacks don’t target protocols directly. They target people.
Phishing attacks accounted for roughly $311 million of January’s total losses. That’s 78% of the damage coming from social engineering rather than code vulnerabilities.
Moreover, these attacks keep working because they exploit basic human psychology. Someone receives a message that looks like official customer support. They’re told there’s an urgent security issue with their account. They’re given simple instructions to “verify” their wallet.
Then their funds disappear.
Hardware wallet manufacturers like Trezor have repeatedly warned users never to share recovery phrases under any circumstances. Yet attackers keep finding victims willing to hand over that information when properly motivated by fear or urgency.
The $284 million theft proves that even experienced crypto holders with substantial holdings can fall for these tactics. That victim presumably understood basic security practices. They used a hardware wallet specifically to protect against remote attacks.
But social engineering bypassed all those technical safeguards by targeting the weakest link in any security system: the human operator.
What This Means for the Industry
These figures aren’t just statistics. They represent real capital leaving the ecosystem and eroding trust in crypto’s security promises.
For individual users, January’s carnage reinforces several critical lessons. First, no amount of technical security matters if you voluntarily compromise your own credentials. Second, privacy coins like Monero continue to provide safe havens for stolen funds despite regulatory pressure. Third, even “secure” platforms can harbor exploitable vulnerabilities.
For protocols and platforms, the message is equally stark. Known vulnerabilities must be addressed before launch, not discovered in production. Treasury security requires the same scrutiny as user-facing features. And no amount of sophisticated technology can protect against social engineering attacks on end users.
Regulators will likely use these numbers to justify stricter oversight. They’ll point to the Monero conversion as evidence that privacy coins facilitate money laundering. They’ll highlight the repeated exploitation of known vulnerabilities as proof that self-regulation isn’t working.
The industry’s response will determine whether February brings meaningful security improvements or just more of the same preventable losses. Based on January’s track record, I’m not optimistic.
