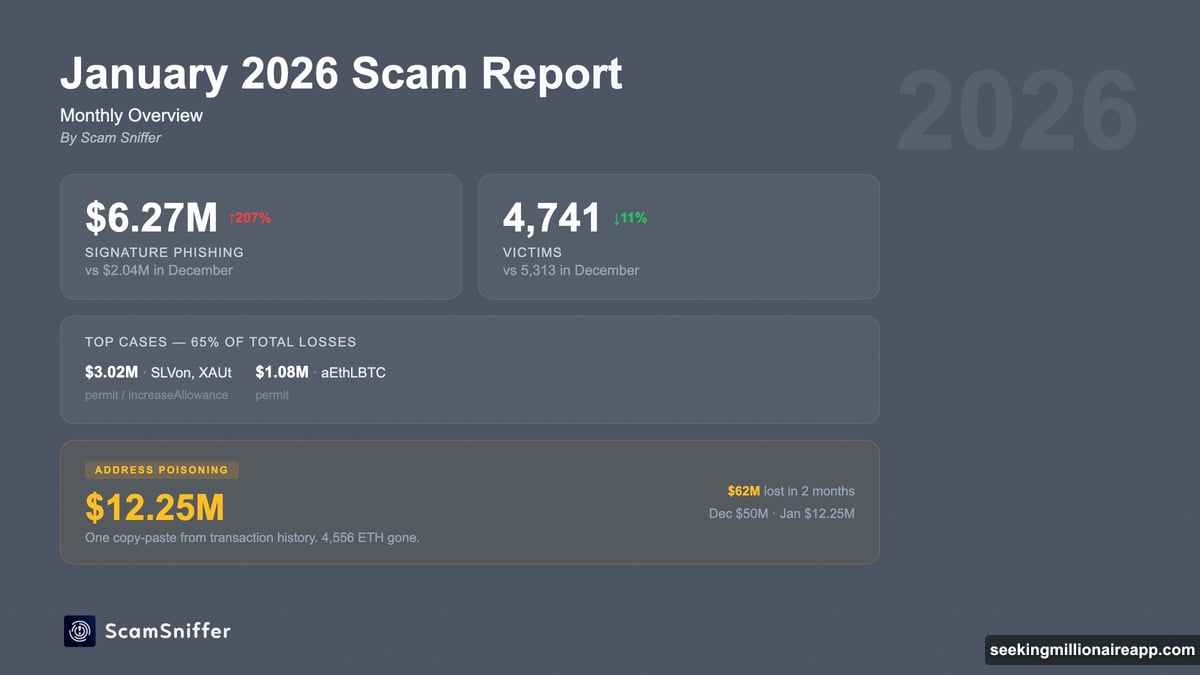
Cryptocurrency phishing attacks evolved dramatically in January 2026. Losses from signature scams alone jumped 207% to $6.3 million.
But here’s what’s really alarming. Attackers shifted their entire strategy. Instead of targeting thousands of small wallets, they now focus on a handful of wealthy victims. Plus, the tactics got significantly more sophisticated.
Two victims accounted for 65% of all signature phishing losses last month. One person lost $3.02 million in a single attack. Meanwhile, another investor lost $12.25 million to address poisoning. That’s not random cybercrime anymore. That’s precision targeting.
Signature Phishing Targets Shrink But Losses Explode
The numbers tell a strange story. Victim counts dropped 11% compared to December. Yet total stolen value surged 207%.
What changed? Criminals stopped wasting time on small retail accounts. Now they research high-value targets and craft personalized attacks. Think of it as moving from spray-and-pray spam to surgical strikes.
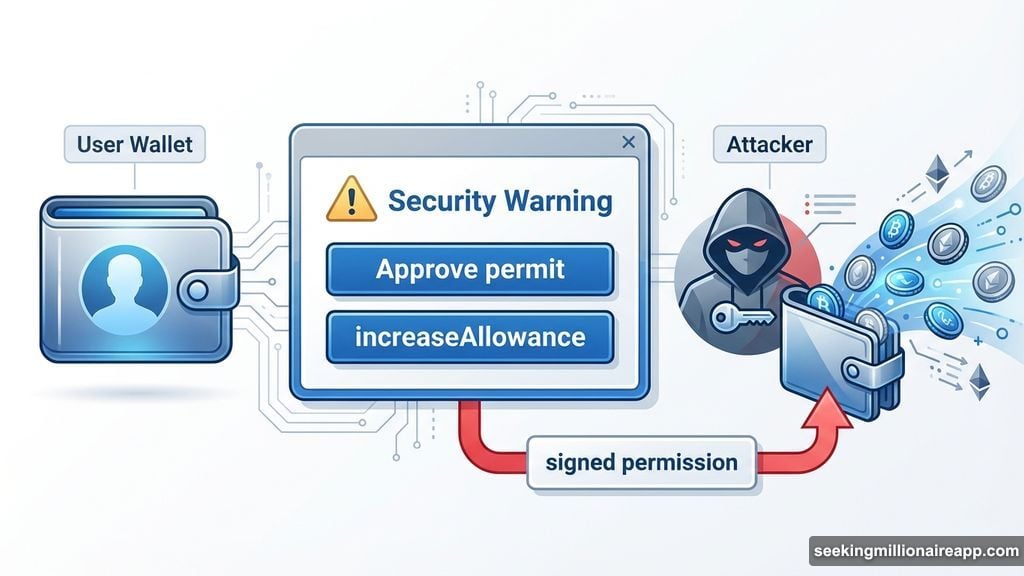
Blockchain security firm Scam Sniffer tracked these trends throughout January. Their data shows attackers primarily exploit “permit” and “increaseAllowance” functions. These smart contract mechanisms sound technical. But the concept is simple.
When you sign one of these malicious permissions, you grant the attacker indefinite access to your wallet. They don’t need your password. They don’t need your private key. You literally authorize them to move your tokens whenever they want.
The scariest part? Most wallet interfaces don’t clearly explain what you’re signing. Users see a popup asking to “approve” something. They click yes without understanding they just handed over complete control of their assets.
Address Poisoning Costs One Victim $12.25 Million
Signature scams weren’t the only threat last month. Address poisoning reached new levels of sophistication.
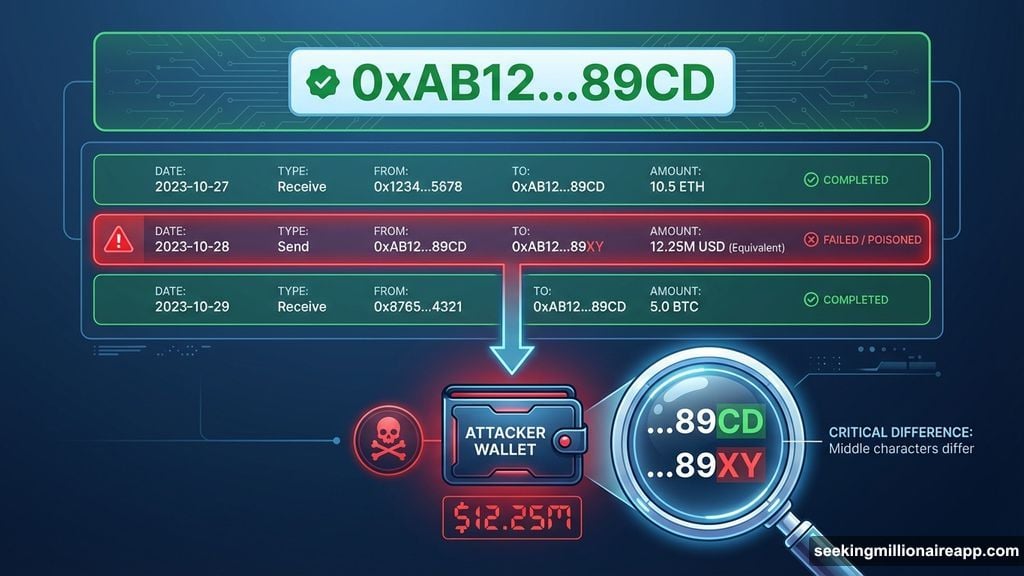
The attack works by exploiting human habits. Most people don’t verify every character in a crypto address. Instead, they glance at the first few and last few characters. If those match a familiar address in their transaction history, they assume it’s correct.
Attackers abuse this shortcut. They generate thousands of “vanity addresses” that mimic legitimate wallet strings. Then they send tiny dust transactions to populate your history with fraudulent addresses.
Later, when you want to send funds to your real wallet, you copy from your history. Except you accidentally grab the poisoned address instead. The transaction goes through immediately. And your funds disappear to an attacker-controlled wallet.
One investor learned this the hard way in January. They sent $12.25 million to what looked like their legitimate address. But a few middle characters differed. By the time they noticed, the money was gone.
Blockchain transactions are irreversible. No customer service can help. No bank can reverse the transfer. That $12.25 million vanished permanently.
5,000 Malicious Addresses Target Safe Wallet Users
The threat got so severe that Safe Labs issued an emergency warning. The company develops Safe, a popular multisig wallet formerly called Gnosis Safe.
Their security team identified a coordinated campaign using approximately 5,000 malicious addresses. These weren’t random scammers working independently. Someone orchestrated a large-scale social engineering operation specifically targeting Safe users.
“We’ve identified a coordinated effort by malicious actor(s) to create thousands of lookalike Safe addresses designed to trick users into sending funds to the wrong destination. This is social engineering combined with address poisoning,” Safe Labs stated in their warning.
The company emphasized that users must verify the complete alphanumeric string of any recipient address. Checking just the first and last characters isn’t enough anymore. Attackers specifically design their addresses to pass that quick visual check.
Safe Labs recommended several protective measures. First, never copy addresses from your transaction history. Always get the address directly from the intended recipient through a verified communication channel.
Second, use address book features in your wallet. Save verified addresses with labels. Then always send to saved contacts rather than pasting addresses.
Third, test large transfers with small amounts first. Send $10 to verify the address works correctly. Then send the full amount only after confirming the test transaction arrived.
Why Attackers Shifted to Whale Hunting
The strategic shift from mass attacks to targeted whaling makes economic sense. Smaller scams face diminishing returns.
Retail investors grew more cautious. They learned to spot obvious phishing attempts. Browser extensions and wallet warnings caught many basic attacks. So scammers needed to work harder for smaller payoffs.
Meanwhile, high-net-worth individuals still make mistakes. Even experienced crypto traders occasionally let their guard down. One moment of inattention can result in million-dollar losses.
Plus, whale hunting requires fewer successful attacks. Stealing $6 million from two victims is easier than stealing $10 from 600,000 victims. The effort-to-reward ratio clearly favors targeting wealthy accounts.
This trend will likely accelerate. As basic phishing defenses improve, attackers will continue focusing resources on fewer, higher-value targets. That means anyone holding significant crypto needs to become extremely paranoid about security.
How to Protect Your Wallet
These attacks succeed because of human error, not technical vulnerabilities. So protection requires changing your habits.
Always verify complete addresses. Don’t trust your eyes to catch differences in middle characters. Copy the address into a text editor. Compare it character by character with a known-good address. Yes, this takes extra time. But it prevents million-dollar mistakes.
Never sign permissions you don’t understand. If a website asks you to approve something and you’re not 100% certain what it does, don’t sign it. Close the tab. Research the function. Ask in community forums. Only proceed after fully understanding what you’re authorizing.
Use hardware wallets for large holdings. Hardware wallets force you to physically confirm transactions on a separate device. That extra step gives you time to verify addresses and permissions. It won’t prevent all attacks, but it adds a crucial layer of protection.
Bookmark legitimate sites. Don’t click links in emails or social media messages. Type URLs manually or use saved bookmarks. Phishing sites often use domains that differ by one letter from legitimate platforms.
Enable transaction notifications. Most wallets can alert you immediately when funds move. If you receive a notification for a transaction you didn’t initiate, you can potentially freeze remaining assets or alert exchanges to block the stolen funds.
The reality is harsh. Crypto security ultimately depends on your vigilance. No company, no protocol, and no insurance will bail you out if you sign a malicious transaction. The responsibility sits entirely on your shoulders.
These January attacks proved that even experienced crypto users can fall victim to sophisticated scams. The attackers are getting smarter. Their techniques are evolving. And the stakes keep rising.
Your defense needs to evolve too. Slow down. Verify everything. Trust nothing. That’s not paranoia. That’s survival in the current crypto landscape.
