Cryptocurrency theft just set a brutal new record. Hackers and scammers walked away with $4.04 billion in 2025, a 34% jump from the previous year.
This isn’t about more attacks. It’s about bigger ones. Criminals shifted tactics, targeting high-value systems instead of spraying attacks everywhere. Plus, recovery efforts failed spectacularly, with only 8% of stolen funds ever recovered.
The numbers tell a stark story. While attack frequency dropped, damage per incident exploded. Let’s break down what went wrong and why 2026 could be even worse.
North Korea’s $1.4 Billion Payday
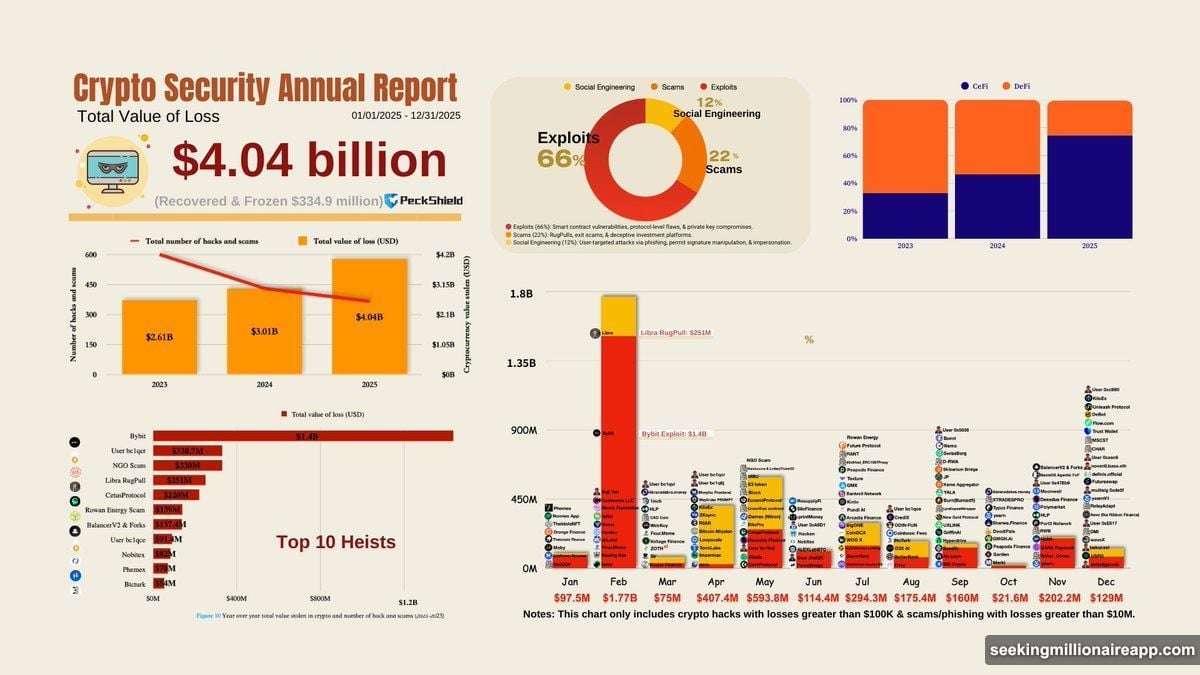
The Bybit hack dominated 2025’s theft statistics. North Korea’s Lazarus Group drained over $1.4 billion from the exchange in a single attack.
That’s not a typo. One hack. One perpetrator. Over a billion dollars gone.
This incident alone accounted for roughly 35% of the year’s total crypto theft. The sophistication level was staggering. Lazarus bypassed multiple security layers, suggesting they spent months planning the attack.
Moreover, the timing was deliberate. February 2025 saw $1.77 billion stolen across all incidents, with Bybit representing the overwhelming majority. So while other attacks occurred that month, Bybit’s losses dwarfed everything else combined.
Recovery? Almost impossible. North Korea operates outside international law enforcement reach. Once funds moved through their laundering networks, tracking became nearly futile.
Rug Pulls and Protocol Exploits Drain Hundreds of Millions
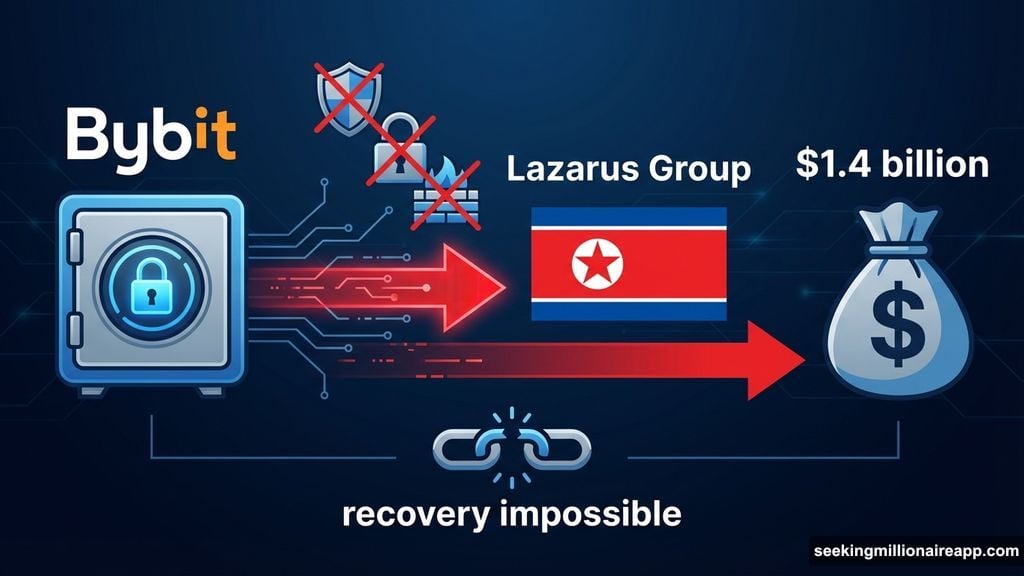
Beyond state-sponsored attacks, traditional crypto scams surged dramatically. The Libra Token rug pull cost investors $251 million when developers vanished with user funds.
Rug pulls work because they exploit trust. Projects build legitimacy over months, attract millions in investment, then creators disappear overnight. Investors wake up holding worthless tokens while founders cash out through complex laundering schemes.
Cetus Protocol suffered differently. This decentralized exchange on the Sui blockchain lost over $200 million through a technical exploit. Attackers found vulnerabilities in the protocol’s smart contract code, allowing them to drain liquidity pools before anyone could react.
Then there’s Nobitex. Iran’s largest crypto exchange lost $81.7 million after Predatory Sparrow, a hacktivist group, breached their systems. This attack combined political motivation with financial theft, showing how geopolitical tensions increasingly target crypto infrastructure.
These incidents reveal a pattern. Whether through code exploits, social engineering, or outright scams, attackers found multiple paths to massive paydays.
Social Engineering Explodes as Primary Attack Vector
Technical exploits still caused the most damage in dollar terms. But social engineering attacks grew fastest year-over-year.
Scam-related losses hit $1.37 billion in 2025, up 64% from 2024. That’s almost double the growth rate of technical exploits. So while code vulnerabilities grab headlines, human manipulation is scaling faster.
How does this work? Phishing attacks impersonate legitimate platforms. Users receive emails or messages that look identical to official communications. They click links, enter credentials, and instantly compromise their accounts.
PeckShield’s report shows 12% of total losses came from these human-focused attacks. That might sound small. But consider the trend. Social engineering grew 64% while total theft grew 34%. So this attack vector is gaining market share rapidly.
Plus, these attacks require less technical skill. You don’t need to find zero-day exploits or crack encryption. You just need convincing fake websites and enough targets. That lowers barriers for criminals, expanding the threat pool.
The Betterment attack in early 2026 demonstrates this perfectly. Attackers tricked users of a legitimate investment platform into revealing credentials. No fancy hacking required. Just good social engineering.
Recovery Efforts Collapsed in 2025
Here’s the really bad news. Stolen crypto rarely comes back.
Only $335 million was recovered or frozen in 2025. That’s down from $489 million recovered in 2024. So while theft increased 34%, recovery decreased 31%. The gap is widening fast.
Why the decline? Laundering techniques improved dramatically. Criminals now use mixers, privacy coins, and decentralized exchanges to obscure fund flows. By the time law enforcement identifies stolen assets, they’ve moved through a dozen jurisdictions and conversion steps.
Plus, international cooperation remains limited. North Korea operates with impunity. Many countries lack crypto-specific investigation capabilities. And jurisdictional disputes slow response times to a crawl.
The recovery rate dropped to roughly 8% in 2025. For every dollar stolen, only eight cents came back. Those odds encourage more attacks, not fewer.
Meanwhile, centralized exchanges represent obvious targets. They hold billions in assets with single points of failure. One compromised private key or social engineering success gives attackers access to massive treasure troves.
Monthly Pattern Shows Concentrated Risk
Theft wasn’t evenly distributed across 2025. February’s $1.77 billion loss dominated the year, primarily due to Bybit. October saw the lowest monthly losses at just $21.6 million.
This volatility matters. It suggests attackers time operations carefully, possibly coordinating multiple exploits when security attention is divided. February likely saw heightened activity because attackers identified vulnerabilities across multiple platforms simultaneously.
Then November losses climbed again. After October’s quiet period, criminals returned with renewed attacks. This on-off pattern makes defense planning difficult. You can’t maintain maximum security posture year-round without burning out teams and budgets.
Furthermore, 2026 started badly. Just 13 days in, two major exploits occurred—the Truebit hack and the Betterment social engineering attack. So the pattern continues, with no slowdown in sight.
Why 2026 Could Be Even Worse
Several factors suggest 2026 might break 2025’s record again. First, attack sophistication keeps rising. State-sponsored groups like Lazarus develop capabilities that criminal gangs later adopt. So techniques that worked in 2025 will spread to more attackers in 2026.
Second, the crypto market is growing. More value locked in protocols means bigger potential paydays. Total value locked in DeFi exceeded $150 billion in early 2026. That’s billions more than previous years, creating more attractive targets.
Third, security improvements lag attack evolution. Most protocols still run code written years ago. Audits happen once, but attackers probe continuously. So defenders fix known vulnerabilities while new ones emerge daily.
Fourth, social engineering will scale further. As technical defenses improve, human-focused attacks become more attractive. Training users to spot scams is harder than patching code. So expect phishing and impersonation to grow even faster in 2026.
Finally, recovery capabilities aren’t improving. Law enforcement budgets and expertise aren’t keeping pace with crypto’s growth. International cooperation remains weak. And privacy-enhancing technologies make laundering easier every year.
Three Things That Must Change Now
The crypto industry needs immediate action to reverse these trends. Wishful thinking won’t cut it.
First, centralized exchanges must adopt insurance requirements. If you hold billions in customer assets, you should carry coverage against theft. Insurance companies would then force better security practices through audits and requirements. That creates market pressure for improvement.
Second, multi-signature authentication should become mandatory for large transactions. Single private keys represent catastrophic risk. Requiring multiple parties to approve significant transfers adds friction attackers can’t easily overcome. Yes, it’s less convenient. But losing $1.4 billion is less convenient.
Third, international task forces need real funding and authority. Current efforts are fragmented and under-resourced. A dedicated, well-funded international crypto crime unit with arrest authority across jurisdictions could recover significantly more stolen assets and deter future attacks.
These solutions exist. Implementation is the challenge. But without major changes, expect $5 billion stolen in 2026, $7 billion in 2027, and so on.
The choice is clear: invest in security now or watch theft escalate indefinitely.
