Iran just moved over $2 billion in cryptocurrency to fund proxy operations and dodge Western sanctions. That’s not speculation. That’s documented blockchain activity tracked by Chainalysis.
The money flowed directly to groups the US labels as terrorist organizations. Hezbollah, Hamas, and the Houthis all received funds through crypto channels. Meanwhile, the Islamic Revolutionary Guard Corps (IRGC) orchestrated the entire operation.
But Iran isn’t alone in weaponizing digital assets. Russia, North Korea, and Chinese crime networks turned 2025 into the most dangerous year for crypto yet.
Illicit Crypto Transactions Exploded 162%
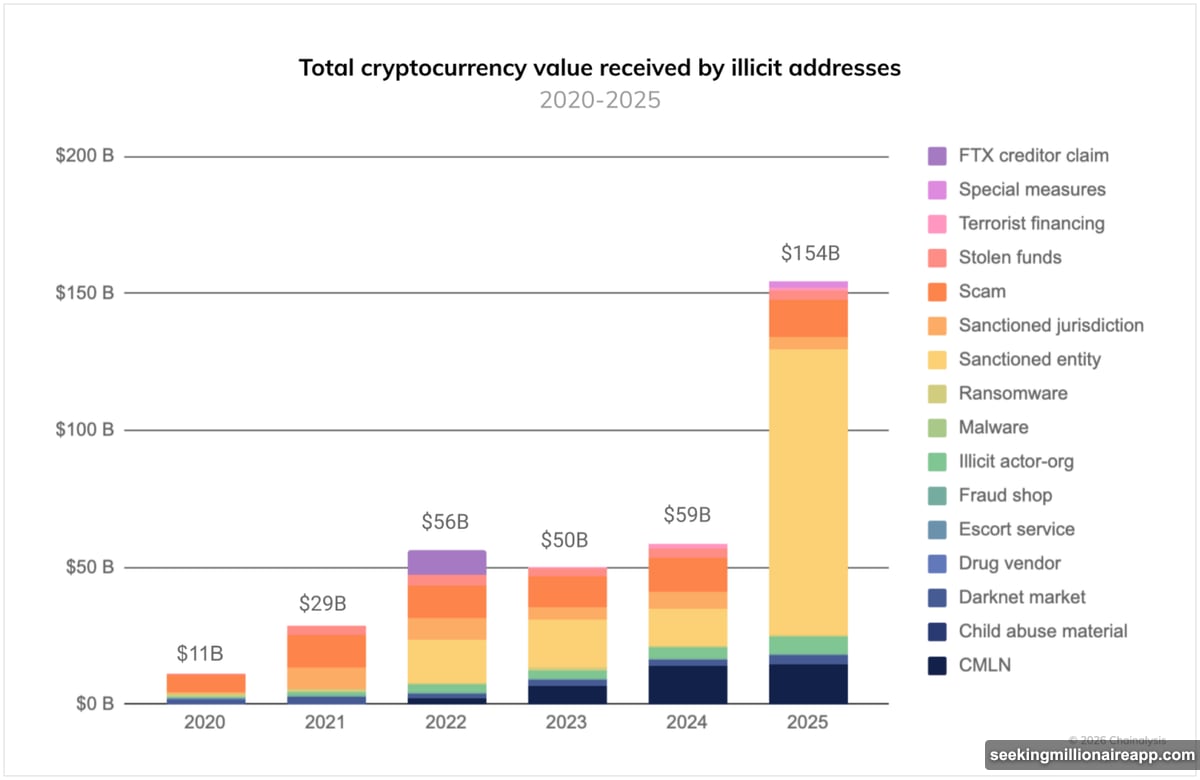
Total illicit cryptocurrency activity hit $154 billion in 2025. That’s a 162% jump from the previous year, according to Chainalysis data.
Three countries drove most of this surge. Russia led the pack with its new A7A5 stablecoin. North Korean hackers stole $2 billion through increasingly sophisticated attacks. Plus, Chinese money laundering networks professionalized crypto crime at scale.
Here’s the scary part. These figures only capture known illicit addresses. The real numbers are likely higher since blockchain analytics can’t identify every malicious wallet.
The West keeps imposing sanctions. Yet sanctioned countries keep finding ways around them through crypto. So traditional financial restrictions lose effectiveness when money moves on-chain.
Russia’s A7A5 Token Changed Everything
Russia accounted for the largest share of illicit crypto activity in 2025. Their secret weapon? The A7A5 stablecoin pegged to the Russian ruble.
Transactions involving A7A5 reached at least $93 billion last year. That single token drove a nearly sevenfold increase in crypto activity among sanctioned entities.
Why does a Russian stablecoin matter? Because it created a parallel financial system immune to Western banking controls. Companies and individuals under sanctions could suddenly transact billions without touching SWIFT or traditional payment rails.
Moreover, the A7A5 token legitimized crypto use for sanctions evasion. Other countries watched Russia’s success and started planning their own digital currency strategies.
The timing wasn’t coincidental. Russia launched A7A5 shortly after facing expanded sanctions over the Ukraine conflict. So the token served as a direct countermeasure to Western financial pressure.
North Korean Hackers Had Their Best Year Ever
North Korean cybercriminals stole approximately $2 billion in cryptocurrency during 2025. That marks their most damaging year on record.
But the total value stolen only tells part of the story. The real concern is their evolving sophistication.
These hackers now use advanced social engineering, zero-day exploits, and complex money laundering chains. They’ve moved beyond simple phishing attacks to orchestrating multi-stage operations that can drain entire exchanges.
Take their typical approach. First, they compromise a crypto project through insider access or social engineering. Then they drain funds across multiple chains simultaneously. Finally, they launder proceeds through Chinese money laundering networks and privacy coins.
The DPRK funnels these stolen funds directly to weapons programs and military operations. So every successful hack doesn’t just hurt crypto projects. It literally finances nuclear development and ballistic missile tests.
Plus, their success rate keeps improving. North Korean groups now successfully breach targets that have strong security measures in place. That suggests they’re acquiring better tools and recruiting top talent.
Chinese Crime Networks Professionalized Everything
Chinese money laundering networks (CMLNs) emerged as the infrastructure backbone of crypto crime in 2025. They didn’t just participate in illicit activity. They industrialized it.
These networks now offer laundering-as-a-service to other criminals. Need to clean stolen crypto? CMLNs provide turnkey solutions with competitive rates and fast turnaround times.

Moreover, they’ve diversified beyond simple money laundering. CMLNs now support fraud operations, scam infrastructure, North Korean hacking proceeds, sanctions evasion, and even terrorist financing.
Platforms like Huione Guarantee evolved into full-service criminal marketplaces. You can find everything from fake IDs to laundered crypto to human trafficking services on these platforms.
Here’s what makes CMLNs particularly dangerous. They operate with near-impunity from bases in Southeast Asia. Countries like Cambodia and Myanmar lack the resources or political will to shut them down.
So these networks established permanent infrastructure for crypto crime. They’re not opportunistic criminals. They’re organized businesses with customer service, marketing, and operational efficiency.
Crypto Crime Turned Physically Violent
The Chainalysis report highlighted a disturbing new trend. Digital crime increasingly correlates with physical violence.
Physical attacks on bitcoin holders jumped 33% in 2025. Violent crypto robberies and kidnappings surged 169% during the same period.
Why the spike? Public wallet exposure makes crypto holders visible targets. Criminals don’t need to hack wallets anymore. They just need to identify wealthy holders and coerce them physically.
These “wrench attacks” typically start with doxxing. Someone discovers a person holds significant crypto through blockchain analysis or social media. Then criminals kidnap or threaten the holder until they transfer funds.
Moreover, Chinese crime networks now connect crypto operations to human trafficking. Victims get forced to work in scam compounds where they facilitate crypto fraud under threat of violence.
The blockchain transparency that makes crypto innovative also makes holders vulnerable. Every transaction lives permanently on-chain for anyone to analyze.
Iran’s Proxy Network Runs on Digital Money

Back to Iran’s $2 billion operation. The IRGC didn’t just move money for itself. It funded an entire network of militant proxy groups through cryptocurrency channels.
Hezbollah in Lebanon, Hamas in Gaza, and the Houthis in Yemen all received crypto funding. These groups couldn’t access traditional banking after US sanctions. So Iran pivoted to digital assets.
Here’s how the operation likely worked. The IRGC acquired crypto through mining operations or exchanges in sanctioned-friendly jurisdictions. Then they transferred funds to wallets controlled by proxy groups. Finally, those groups converted crypto to local currency through underground exchanges or peer-to-peer networks.
The $2 billion figure only accounts for US sanctions designations. If you include activity flagged by other countries, the total could be significantly higher.
Plus, Iran operates extensive cryptocurrency mining infrastructure. Some estimates suggest they mine enough bitcoin annually to fund substantial operations even without buying crypto on exchanges.
The Numbers Keep Getting Worse
Despite everything, Chainalysis clarified that illicit transactions still represent a small percentage of total crypto activity. Most blockchain usage remains legitimate.
But that small percentage now involves massive absolute values. When total crypto market cap exceeds $3 trillion, even 5% illicit activity equals $150 billion in dirty money.
The sophistication gap is closing too. Criminals now access the same tools and infrastructure as legitimate users. Privacy mixers, cross-chain bridges, and decentralized exchanges all serve both legal and illegal purposes.
So the crypto industry faces an existential challenge. How do you maintain the permissionless, censorship-resistant properties that make blockchain valuable while preventing sophisticated criminals from exploiting those same properties?
Traditional finance dealt with this through centralized gatekeepers and regulatory oversight. But that approach contradicts crypto’s core values. Yet doing nothing increasingly links digital assets to terrorism, sanctions evasion, and violent crime.
The urgency of solving this problem just reached unprecedented levels. What happens in 2026 will determine whether crypto becomes a tool for human freedom or a weapon for the world’s most dangerous actors.
